2FA Accounts Migration: 9 Proven Steps to Securely Move Your Authentication Accounts
Move your 2FA safely — swift, secure, and stress-free.
Have you ever swapped phones and been locked out of a bank, email or work account because you could not move your authentication app? This guide solves that problem. It gives a practical, tested plan for a safe 2FA accounts migration so you keep access, avoid lockouts and harden security while you move. Follow the steps exactly, test as you go, and treat backup codes as sacred paperwork.

Table of Contents
Why a careful 2FA accounts migration matters
Multi-factor authentication dramatically reduces account takeover risk. A planned 2FA accounts migration avoids the long outages that follow losing access to an authenticator app. Government and security agencies recommend MFA as a core defence for accounts and services. See CISA’s guidance on why MFA matters for organisations and individuals. (CISA)
Pre-migration checklist (quick wins)
Before you touch either phone:
- Do not wipe or factory reset the old device until all accounts are tested on the new device.
- Collect and securely store backup codes for every account (Google, Microsoft, banks, social, and work accounts). Store them in an encrypted password manager and keep a physical copy in a safe place. (Google’s backup codes page explains how to generate and use these.) (Google Help)
- Install the same authenticator app(s) on the new device ahead of time (Google Authenticator, Microsoft Authenticator, Authy, or your chosen manager).
- Ensure you know the account passwords and that recovery email or phone numbers are current.
- Update both devices’ OS and apps to the latest versions.
- Charge both phones and use a trusted network (home Wi-Fi or mobile hotspot).
- Create an inventory: a spreadsheet (or simple list) with account name, 2FA method used, and backup codes present? (yes/no), priority (high/medium/low).
- See our guide: How to choose the best authenticator app.
- Read our enterprise checklist: MFA rollout for organisations.
- Tool notes: Using password managers for TOTP.
These steps act as your migration script — follow them to reduce errors and speed recovery if something goes wrong.
How to perform a 2FA accounts migration with Google Authenticator
Google Authenticator provides an in-app transfer flow for exporting/importing accounts via QR codes. The easiest official flow is: export selected accounts on the old phone (which displays QR codes) and scan them with the new phone. See Google’s official guide for transferring accounts. (Google Help)
Step-by-step (Google Authenticator)
- On the old phone, open Google Authenticator → Menu → Transfer accounts → Export accounts. Unlock the app to continue. (Google Help)
- Select the accounts you wish to move and generate the QR code(s).
- On the new phone, install Google Authenticator → Menu → Transfer accounts → Import accounts → Scan QR code. Scan the QR code(s) displayed on the old phone.
- For each account, sign into the service and confirm that the codes from the new device work. Test at least three critical services first (email, bank, workplace).
- Once all tests pass, remove the exported data from the old phone and delete any temporary QR images.
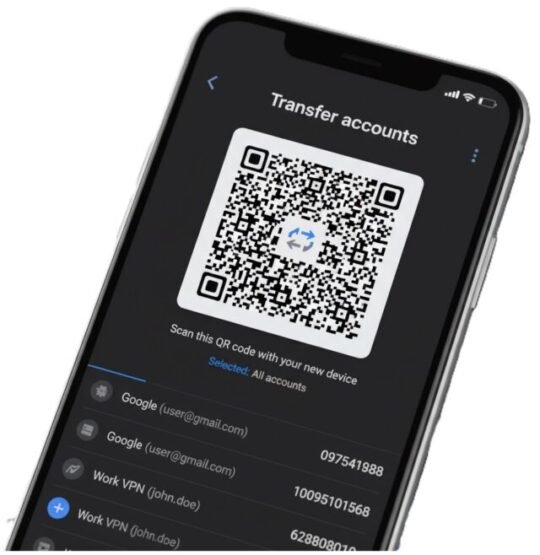
Key tip: If export shows multiple QR codes, scan them all. Avoid taking photos of QR codes that you store insecurely.
2FA accounts migration using Microsoft Authenticator (cloud backup)
Microsoft Authenticator offers encrypted cloud backup and restore through your Microsoft account. This makes migration very straightforward: enable Cloud Backup on the old phone, then restore on the new phone using the same Microsoft account. Microsoft’s support pages explain backup and restore steps in detail. (Microsoft Support)
Step-by-step (Microsoft Authenticator)
- On the old phone, open Microsoft Authenticator → Settings → Cloud Backup → turn on and confirm backup. Wait for completion. (Microsoft Support)
- Install Microsoft Authenticator on the new phone → choose Restore from backup (or Begin recovery) → sign in with the same Microsoft account used for backup. Follow prompts to restore tokens. (Microsoft Support)
- Test the codes for high-priority accounts immediately after restore.
- Revoke or remove device entries for the old phone in account security settings after you’re satisfied.
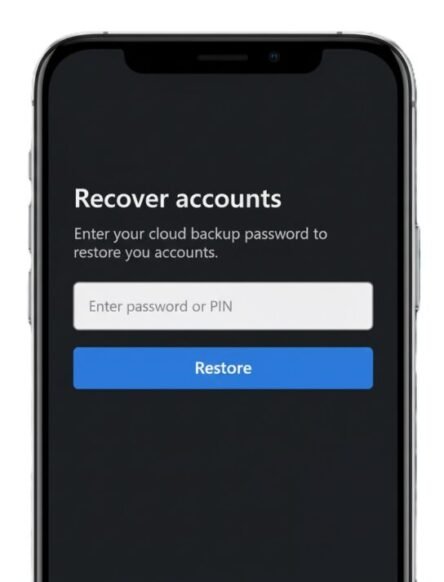
Note: If you rely on a work/school Azure AD account, some admin policies may limit backup/restore. Speak to your IT team for enterprise enrolment flows. (See our enterprise guide.) MFA rollout for organisations
2FA accounts migration with Authy: multi-device and backups
Authy is purpose-built for multi-device sync and encrypted cloud backups. Enable Authy backup or multi-device support on your old device, set a strong backup password, then install and register Authy on the new device using the same phone number. Authy’s support documentation explains enabling backups and syncing devices. (Twilio Help Center)
Steps (Authy)
- On the old device, open Authy → Settings → enable Backups (create a backup password) and/or Multi-device if you want active sync. (Twilio Help Center)
- On the new device, install Authy → register with the same phone number → approve the new device (if multi-device is enabled) or restore from backup with your backup password.
- Test codes before revoking access from the old device.
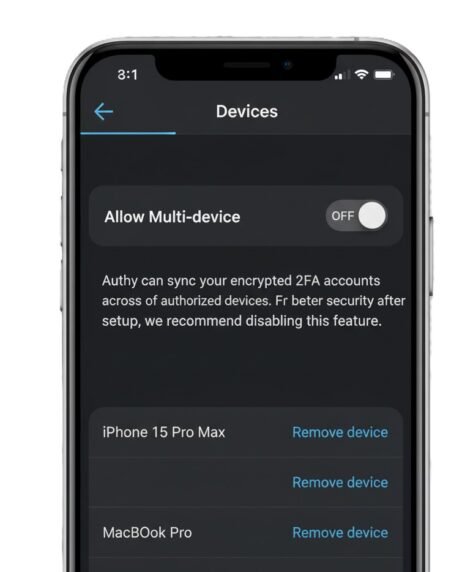
Security note: your Authy backup password is critical. If you forget it, Authy cannot decrypt backups for you.
When you no longer have the old device — recovery paths
If your old phone is lost or broken, recovery is still possible — but rely on pre-prepared recovery options.
Primary recovery options
- Backup codes. Most providers issue one-time backup codes you can use if the authenticator is unavailable. (See Google’s backup codes documentation.) (Google Help)
- Account recovery forms. Use provider recovery flows — you’ll typically need to prove account ownership via recovery email, phone, or identity details.
- Admin reissue. For workplace accounts, ask IT to reset MFA or issue temporary access.
- Hardware keys and secondary methods. If you registered a security key or an alternative second factor, use those to regain access.
If you have nothing prepared, expect longer support cycles and requests for proof of identity or recent account activity.
Validate, test, and finalise: migration audit
A migration is only complete once everything is verified.
Validation checklist (audit):
- Sign in to each account using the new device’s codes and mark it as tested.
- Record which accounts require manual re-setup.
- Remove old device entries where possible from each account’s security settings.
- Rotate the backup password for cloud backups after migration (if using Authy or a similar service).
- Securely delete any temporary QR images or exported files.
Testing reduces the chance of account lockouts and ensures the 2FA accounts migration is durable.
Troubleshooting: recipes for common problems
Problem: Codes from the new phone are rejected.
- Likely cause: clock drift. Time-based one-time passwords (TOTP) depend on accurate device clocks. Sync both devices to the network time and retry. (See provider troubleshooting guides.) (Google Help)
Problem: Cloud backup restore fails (Microsoft).
- Confirm you are signed into the same Microsoft account used for backup and that Cloud Backup completed on the old device. Check the recovery/restore guide on Microsoft Support. (Microsoft Support)
Problem: You cannot sign in and you do not have backup codes.
- Use account recovery flows for each service and prepare ownership evidence (recent transactions, creation date, registered devices). For workplace accounts, escalate to your IT admin.
Problem: Some accounts won’t export.
- Some services intentionally block TOTP export for security reasons. You must re-enrol those accounts manually via their “Set up authenticator” or security page.
Advanced options & enterprise scale-up
Hardware security keys (FIDO2)
For high-value accounts, add FIDO2 hardware keys (YubiKey, etc.). These often require re-registration at each service.
Password managers with TOTP support
Many password managers now store TOTP secrets. If you use one, follow its export/import flow to perform a consolidated 2FA accounts migration. (See our tools guide.) Using password managers for TOTP
Enterprise mass migration
Organisations should use identity and device management tools that support MFA lifecycle and automated enrolment. A staged plan, inventory, and staff communications are essential.
Case study: IT admin migrating 60 members of staff
Plan highlights:
- Inventory accounts and prioritise.
- Use Microsoft Authenticator cloud backup where Microsoft accounts are used. (Microsoft Support)
- Run on-site QR transfer sessions for Google Authenticator users. (Google Help)
- Validate by running batch sign-ins. Result: downtime under 60 minutes per user.
FAQs
Q1: What is a 2FA accounts migration?
A1: A 2FA accounts migration transfers your two-factor authentication tokens and settings from one device to another — by exporting/importing tokens, restoring cloud backups, or re-enrolling accounts.
Q2: Can I transfer Google Authenticator to a new phone without the old phone?
A2: Only if you previously enabled Google’s sync/backup features or have backup codes. Otherwise, you must use each provider’s account recovery. See Google’s support page for backup codes and sign-in help. (Google Help)
Q3: How long does a typical 2FA account migration take?
A3: For a personal user with under 20 accounts, plan 30–90 minutes, including testing. Organisational migrations require planning and staging.
Q4: Are cloud backups safe for authentication apps?
A4: Reputable apps encrypt backups. Cloud backups are convenient, but treat the recovery account and backup password like high-value credentials. Authy and Microsoft document encryption and backup workflows; read the provider guidance to understand limits. (Twilio Help Center)
Q5: What should I do immediately after migration?
A5: Test every account, revoke old device access where possible, secure backup codes, and update your inventory.
Key takeaways:
- Plan your 2FA accounts migration before swapping devices.
- Use app-specific flows: export/import for Google Authenticator, cloud backup/restore for Microsoft Authenticator, and Authy for multi-device convenience. (Google Help)
- Keep backup codes and recovery options stored securely.
- Test everything and only wipe the old device once you confirm access.
If this guide helped, kindly subscribe to our newsletter for security insights that will come in handy for you right when you need them. Feel free to share to protect others, and save the migration checklist for your next device change. Thank you.







Leave a Reply